What is cyber threat intelligence? A practical overview for businesses

Cyber threat intelligence (CTI) is the process of collecting, analysing, and acting on information about cyber threats that could harm your organisation. Rather than just reacting to breaches after the fact, cyber threat intelligence data tells you who’s targeting organisations like yours, what methods they’re using, and how to stop them.
If you would like to learn more about Zensec’s cyber threat intelligence services, please visit our dedicated landing page.
Most businesses generate thousands of security alerts daily. But without context, it’s nearly impossible to know which ones represent genuine dangers.
In this guide, we’ll explore what threat intelligence is, how each type serves a distinct purpose within your organisation, and how it supports faster, more effective responses to ransomware and other cyberattacks.
What is cyber threat intelligence in practice?
Think of it like weather forecasting for cybersecurity. Just as meteorologists analyse atmospheric data to predict storms, threat intelligence analysts examine patterns in cyberattack data to anticipate what threats are heading your way.
The intelligence tells you not just that rain is coming, but what kind of storm to expect and how to prepare for it.
When people talk about threat intelligence, they’re usually referring to three key elements:
- Information about who the attackers are
- What methods they use to break into systems
- Measures you can take to stop them
This context is what separates useful intelligence from the flood of security alerts that most companies deal with every day.
Why is cyber threat intelligence important?
Most businesses today generate thousands of security alerts each day, but not all of them represent real threats.
By integrating threat intelligence, you separate genuine dangers from false alarms, enabling your team to focus on what actually matters.
Here’s the practical difference it makes: without CTI, you’re essentially defending blindly, treating every potential threat the same way.
With it, you know that (say) ransomware group X is actively targeting companies in your industry, using vulnerability Y, and typically demands £500,000 in Bitcoin. That specificity changes everything about how you prepare and respond.
The shift from reactive to proactive defence is the real value here:
Threat intelligence enables organisations to be proactive by patching vulnerabilities and blocking malicious domains before attacks occur, and by tailoring incident response plans. If an attack does happen, it allows teams to detect it faster and contain it more effectively.
For businesses facing ransomware specifically, intelligence about which groups target your sector and how they operate can mean the difference between a minor disruption and a catastrophic breach.
You’ll know what to watch for, what data attackers typically steal, and what their negotiation tactics look like if the worst happens.
The types of cyber threat intelligence
| Intelligence Type | What It Focuses On | Who Uses It / Why It Matters |
|---|---|---|
| Strategic Threat Intelligence | High-level trends, attacker motivations, geopolitical factors, industry-wide risks, regulatory changes | Executives and leadership teams use it to make budget, policy, and long-term risk decisions |
| Operational Threat Intelligence | Specific threat actors, campaigns, TTPs, preferred tools, targeting patterns | Incident responders and SOC teams use it to identify attackers and anticipate next steps during active incidents |
| Tactical Threat Intelligence | Technical indicators such as malicious IPs, domains, URLs, file hashes, malware signatures | Security engineers and automated tools use it to detect, block, and prevent known attacks |
| Technical Threat Intelligence | Malware code, exploit details, vulnerabilities, and attacker infrastructure | Researchers and forensic analysts use it to understand attack mechanics and investigate sophisticated threats |
Threat intelligence operates at different levels, each serving different audiences within your organisation.
Understanding these types helps you figure out what intelligence your team actually needs.
Strategic threat intelligence
Strategic intelligence is the big-picture view designed for executives and board members who make budget and policy decisions.
It focuses on trends rather than technical details—things like which nation-state groups are becoming more active, how ransomware tactics are evolving, or what new regulations might affect your security requirements.
You might use a strategic threat intelligence solution to justify increasing your security budget or to assess risks when expanding into new markets. It answers questions like “What are the major threats to our industry?” and “How is the threat landscape changing?”
Operational threat intelligence
Operational intelligence dives into specific threat actors and their campaigns. It tells you not just that attacks are happening, but how particular groups operate, what tools they prefer, and what their goals typically are.
For incident response teams, this level is invaluable during active attacks. If security professionals can identify which ransomware group is targeting you, operational intelligence reveals their typical behaviour patterns, helping you anticipate their next moves and plan your response accordingly.
Tactical threat intelligence
Tactical intelligence comprises specific technical indicators that security tools can use to detect attacks. This includes things like malicious IP addresses, suspicious domain names, file hashes of known malware, and email addresses used in phishing campaigns.
Most security teams interact with tactical intelligence daily, often without realising it. When your email filter blocks a phishing attempt or your firewall drops traffic from a malicious IP, that’s tactical intelligence at work. These indicators feed directly into security tools, enabling automated detection and blocking.
Technical threat intelligence
Technical intelligence examines the detailed mechanics of how attacks work—the actual code in malware, the specific vulnerabilities exploited, and the infrastructure attackers use.
Security researchers and forensic analysts use these threat intelligence tools to understand exactly how malicious software functions or how attackers bypass security controls.
While technical intelligence is highly specialised, it becomes critical during complex investigations or when dealing with sophisticated, targeted attacks.
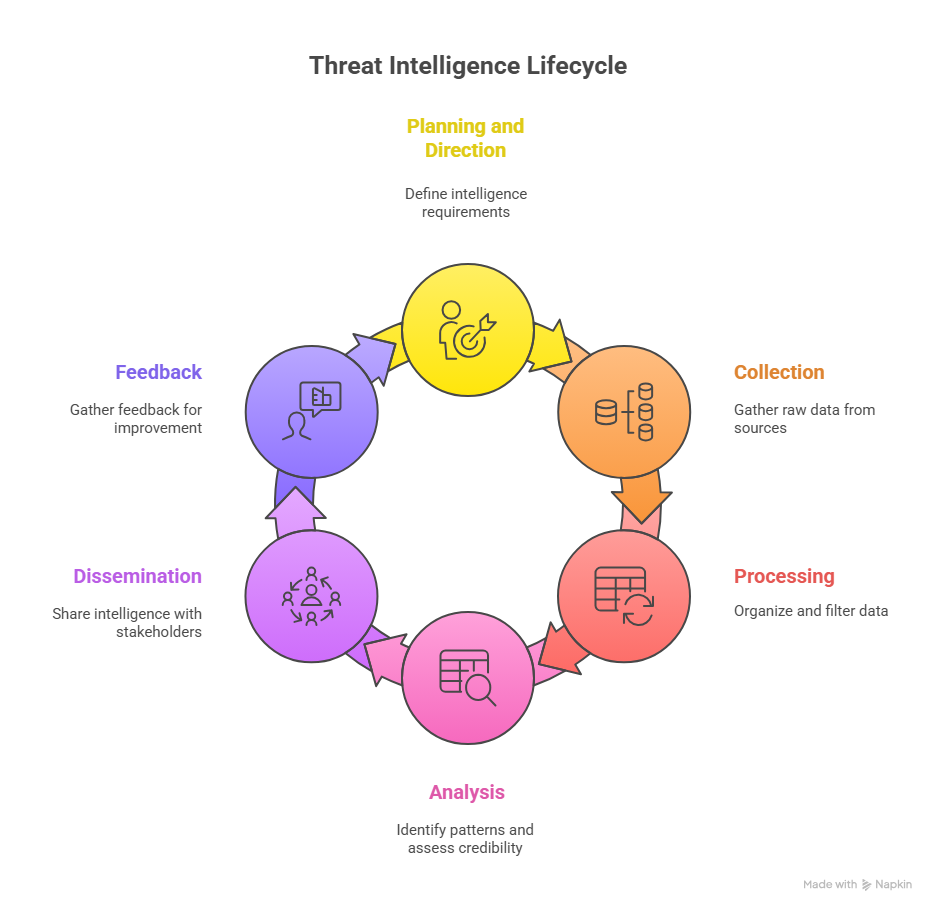
The threat intelligence lifecycle
When you leverage threat intelligence, remember it’s a continuous process that turns raw data into actionable insights.
Rather than a one-time project, it’s an ongoing cycle that adapts as threats evolve.
Planning and direction
The lifecycle starts with defining what questions your intelligence program needs to answer. You should know which ransomware groups target businesses like yours, which vulnerabilities attackers are actively exploiting, or whether your employees’ credentials have appeared in recent data breaches.
These intelligence requirements drive everything that follows. Without clear questions, you’ll collect mountains of data but struggle to turn it into practical guidance.
Collection
Collection means gathering raw data from multiple sources, both inside and outside your organisation.
Internal sources include your security logs, incident reports, and network traffic data. External sources include commercial threat feeds, open-source intelligence, information-sharing groups, and monitoring of underground forums where attackers communicate.
The challenge here is casting a wide enough net to capture relevant threats without drowning your team in irrelevant information.
Processing
Raw threat data arrives in different formats from different sources, making it challenging to analyse. Processing involves organising this data into a consistent format, removing duplicates, and filtering out obvious false positives.
Using a cyber threat intelligence platform with automated tools to handle much of this work, correlating indicators and enriching data with additional context.
Analysis
Analysis is where data becomes intelligence. Analysts examine processed information to identify patterns, assess the credibility of different sources, determine what’s relevant to your specific organisation, and draw conclusions about what attackers are likely to do next.
This step requires both technical knowledge and understanding of your environment. The goal is to answer those intelligence requirements you defined at the start.
Dissemination
Intelligence only creates value when it reaches the right people in formats they can use. Technical teams might receive detailed indicator feeds, while executives get summary reports highlighting strategic risks.
Timing matters significantly here. Tactical intelligence about an active attack campaign needs to reach your security operations team immediately, while strategic assessments can follow regular reporting schedules.
Feedback
The cycle closes with feedback from the people using your intelligence. Did it answer their questions? What gaps remain? This feedback shapes the next planning phase, helping your program improve and stay aligned with what your organisation actually needs.
Key components of an effective threat intelligence program
Building a threat intelligence capability requires more than subscribing to a few threat data feeds. You’ll need the right combination of people, processes, and technology.
Skilled analysts
Threat intelligence analysis requires both technical expertise and the ability to translate complex threats into business language that executives understand.
Your analysts examine patterns in attack data, assess the credibility of sources, and determine which threats matter most to your organisation. For example, advanced persistent threats often require immediate mitigation strategies, while minor threats can be monitored.
Clear intelligence requirements
Without defined questions to answer, threat intelligence programs often collect vast amounts of data without producing useful insights. Work with stakeholders to identify what decisions intelligence should inform.
Multiple data sources
Relying on a single intelligence source creates blind spots. Effective programs combine commercial feeds, open-source intelligence, information-sharing communities, and internal security data to build a complete picture.
Integration with security operations
Threat intelligence delivers maximum value when it connects to your existing security tools and workflows. This means feeding tactical indicators into detection systems and using intelligence to guide which vulnerabilities you patch first.
How integrating threat intelligence supports ransomware response
For organisations dealing with ransomware threats, intelligence provides advantages before, during, and after attacks.
Before an incident, intelligence about which ransomware groups target your sector helps you prepare defences and response plans tailored to likely scenarios.
During an active attack, intelligence accelerates response by helping your team quickly identify the ransomware variant and understand its behaviour. Knowing which threat actor group is behind the attack reveals their typical ransom demands, negotiation patterns, and whether they usually delete stolen data or publish it.
After an incident, intelligence helps you understand what vulnerabilities the attackers exploited and whether other organisations in your industry are experiencing similar attacks. This context informs decisions about strengthening defences against future incidents.
Contact our 24/7 incident response team if you’re facing a ransomware attack and need immediate expert assistance.
Common sources of threat intelligence
Threat detection and intelligence come from a diverse mix of sources, each offering different types of information.
- Open-source intelligence (OSINT): Publicly available information from security blogs, researcher publications, and public threat databases provides valuable context about emerging threats. While free, OSINT requires significant effort to collect and validate.
- Commercial threat feeds: Paid services from specialised vendors offer curated, validated, and actionable threat intelligence data with additional analysis. These feeds typically provide higher-quality indicators and faster notification of emerging threats.
- Information sharing communities: Industry-specific groups enable organisations to share threat intelligence with peers facing similar risks. These communities often provide early warning of targeted campaigns.
- Internal telemetry: Your own security tools and incident response activities generate intelligence about threats targeting your specific environment. This internal intelligence is often the most relevant, though it provides limited visibility into broader trends.
- Government sources: Organisations such as the National Cyber Security Centre (NCSC) provide threat intelligence, alerts, and guidance to UK organisations on nation-state threats and critical vulnerabilities.
Threat intelligence platforms and tools
Threat intelligence platforms (TIPs) help organisations aggregate, manage, and operationalise intelligence from multiple sources.
These platforms typically collect and normalise threat data, enrich indicators with additional context, share intelligence with security tools, and enable collaboration across security teams.
When evaluating platforms, consider how well they integrate with your existing security infrastructure, which intelligence sources they support, and whether they align with your team’s technical capabilities.
Some threat intelligence tools focus primarily on tactical indicator management, while others offer broader capabilities for operational and strategic analysis.
Beyond dedicated platforms, many security tools now offer a combined threat intelligence solution.
Security information and event management (SIEM) systems, endpoint detection and response (EDR) solutions, and network security tools increasingly include built-in threat feeds and the ability to consume external intelligence sources.
For organisations without the resources to implement a full platform, starting with focused capabilities—such as integrating a commercial threat feed into existing detection tools—can deliver meaningful value while building toward more comprehensive capabilities over time.
How Zensec uses threat intelligence in ransomware response
At Zensec, threat intelligence forms a core component of our ransomware incident response methodology.
When clients contact us during active attacks, our team immediately leverages current intelligence about ransomware variants, threat actor groups, and attack techniques to accelerate containment and recovery.
Our incident responders maintain up-to-date knowledge of the ransomware threat landscape, including which groups actively target UK organisations, which vulnerabilities they exploit, and how different ransomware families behave.
This intelligence informs every stage of our response, from initial triage through forensic investigation and recovery planning.
Beyond individual incidents, we use threat intelligence to help clients strengthen defences against future attacks.
Our post-incident reviews incorporate relevant intelligence to identify what made an organisation a target, what vulnerabilities attackers exploited, and what specific threats to prioritise going forward.
Please get in touch to learn about our threat intelligence services today.

